D3
Device-Centric Detection and Mitigation of Diameter Signaling Attacks against Mobile Core
Problem
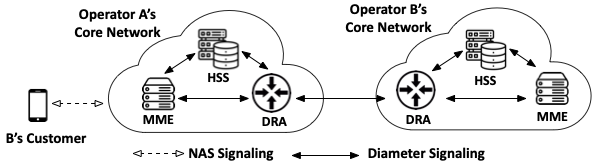
To date, mobile networks are the only large-scale infrastruc- ture that provides ubiquitous data, voice, and texting services. To facilitate the services, signaling messages are frequently exchanged within and among the mobile core networks. These messages query or update the users’ states, so that the mobile networks can serve the users properly. It is thus crucial for a core network to authenticate the signaling messages, especially in roaming scenarios. Otherwise, an attacker can pretend to be another legitimate operator and spoof signaling messages. A major consequential damage is user Denial-of-Service (DoS), where the victim is disabled from accessing certain services.
In the current 4G Long-Term Evolution (LTE) network, Diameter is the de facto protocol used to carry the signaling messages. Despite its proclaimed superior security features, Diameter is reported by multiple sources to be vulnerable to spoofing attacks.
In this project, we first setup a standard-complient LTE testbed with a USRP board (as base station) and a Linux server (as core network). We implement 6 reported Diameter user DoS attacks on our testbed. We study the attack damage and devise the device-centric attacks to detect and mitigate the attacks.
Device-centric Solution D3
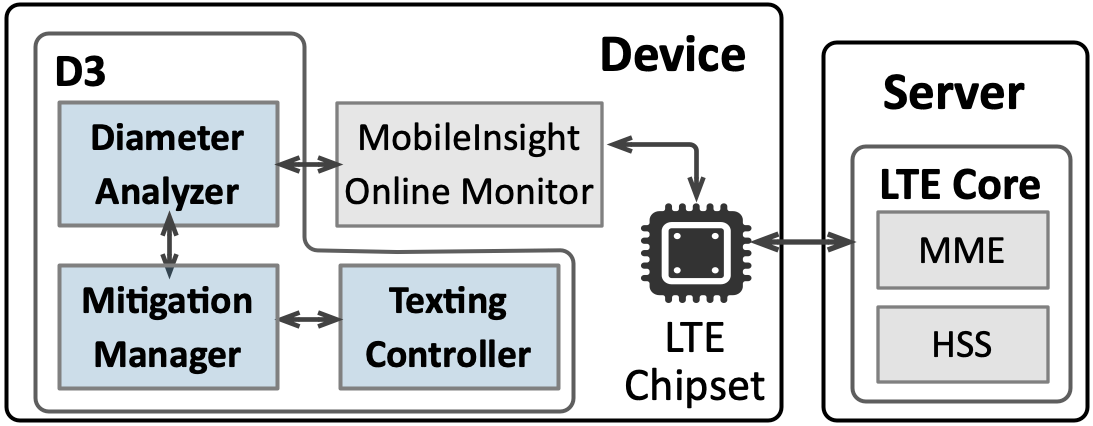
We further propose D3 (Device-centric Defense for Diameter attacks) that can detect such attacks and attempt mitigation in the victim device only. Mobile users can install the software solution without expensive hardware or infrastructure upgrade. The main idea for device-centric de- tection is to analyze the message exchange between the device and network. D3 also actively interacts with the network to further confirm the attack. On the other hand, device- centric mitigation aims at re-synchronizing the state in core network components, where the state inconsistency empowers the Diameter attacks to cause severe DoS damages.
D3 can detect and mitigate the 6 attacks we introduce. For two of the three attack categories, we study how each one results in consequential messages that cause DoS. D3 compares the message contents with those under normal cases. It then accurately detects whether a Diameter attack is underway. For the other category, an active approach is used to check whether an incoming text/call is blocked. Afterwards, D3 takes a device-centric method to mitigate the damage by toggling airplane mode, which will force the device to re-establish connection with the network. When a re-attach is not sufficient, D3 further asks the device to connect to another base station by frequency band locking.
We note that the design of D3 could benefit the security of future 5G core signaling messages. The first phase of 5G plans to reuse the current 4G core, where D3 can directly apply. Although 5G will eventually replace the Diameter with HTTP/2, the trust model is similar to 4G. So an attacker can still forge signaling messages from a lesser operator and launch attacks. Meanwhile, 5G inherits 4G’s message exchange between the network and the device. We can adapt D3 to 5G attack detection without much modification.
Outcome
We implement D3 in Android devices and develop a pro- totype on a Google Pixel XL phone. We evaluate how D3 combats the Diameter attacks. D3 can successfully detect all 6 attacks and mitigate the DoS effects completely in seconds with low overhead. We also show that D3 achieves perfect precision and recall when we mix Diameter attacks with other normal loss of services.
Publications
| Device-Centric Detection and Mitigation of Diameter Signaling Attacks against Mobile Core Zhaowei Tan, Boyan Ding, Zhehui Zhang, Qianru Li, Yunqi Guo, and Songwu Lu, |
Team Members
- Zhaowei Tan (University of California, Los Angeles)
- Boyan Ding (University of California, Los Angeles)
- Qianru Li (University of California, Los Angeles)
- Zhehui Zhang (University of California, Los Angeles)
- Yunqi Guo (University of California, Los Angeles)
- Songwu Lu (University of California, Los Angeles)
Research Support
We gratefully acknowledge research support from the departmental support of UCLA.
