SecVoice
LTE Voice in Peril and Beyond: A Security Perspective on VoLTE and CSFB and More
Overview
This project investigate security implications of 4G LTE voice solutions: VoLTE (voice-over-LTE) and CSFB (circuit-switched Fallback). In this project, we seek to disclose whether both schemes might be harmful to mobile users and/or operators from a security perspective. If so, we aim to pinpoint their root causes, uncover the insights of insecurity and devise defenses that protect from such attacks.
Voice is a simple utility service, yet vital to both mobile operators and phone users. It has been a killer application to mobile networks for decades since its origin. However, as the cellular infrastructure upgrades to Long Term Evolution (LTE), the fourth-generation (4G) mobile technology, voice service is inevitably going through its fast evolution. LTE is packet-switched (PS)-only, all-IP based network. It completely abandons the circuit-switched (CS) design so that the legacy voice solution to 2G/3G networks is not supported over LTE. As a result, two voice solutions are proposed accordingly: CSFB (Circuit-Switched FallBack) and VoLTE (Voice over LTE). CSFB leverages the CS domain in the legacy 3G systems to support voice calls for LTE users. Whenever a call is made, CSFB transfers the call request from the 4G network to the 3G system. Once the call completes, CSFB moves the phone back to the 4G network. In contrast, VoLTE supports voice calls directly in the 4G system. It leverages the Voice-over-IP (VoIP) solution over the Internet, and still offers guaranteed Quality-of-Service (QoS) through resource reservation in LTE networks.
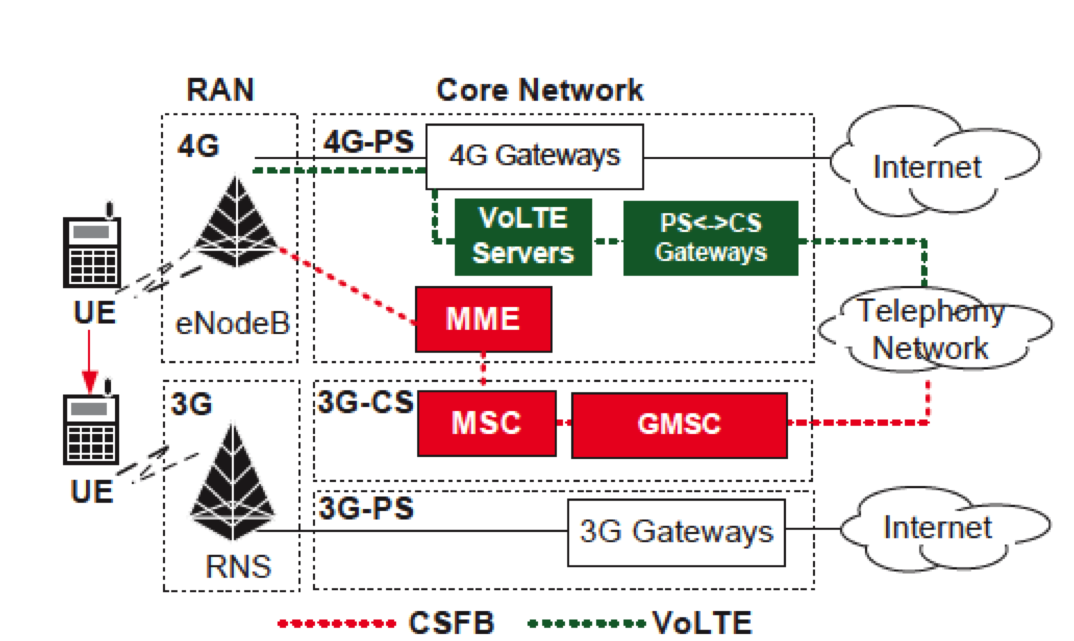
While VoLTE is the ultimate voice solution to LTE, both voice solutions are foreseen to coexist in the long run. CSFB leverages the deployed legacy system and works with most current phone models (whereas VoLTE requires new phones). It thus offers a cost-effective, readily-accessible solution. As the most popular voice solution to date, CSFB has been widely deployed or endorsed by most LTE carriers such as top global carriers (China Mobile, Vodafone, Bharti Airtel, Telefonica, AT&T, T-Mobile, to name a few). On the other hand, VoLTE promises to be the ultimate solution though its current deployment is not as popular as CSFB. In US, a leading VoLTE market, three major operators (AT&T, T-Mobile and Verizon) have started to launch VoLTE until late 2014. Its roll-out is on the way.
We examine whether VoLTE and CSFB exposes new and unexpected threats. Our study stems from a simple rule of thumb in that any major change is probably a source for insecurity. With the nontrivial changes from CS to PS in its core technology, VoLTE may interfere with other system components, thereby inducing new loopholes. For CSFB, it has to trigger 3G-4G handoff, which is originally designed to support mobility and universal coverage, but now is open to any caller, even without permission from the callee.
Research Progress
Threats from CSFB
CSFB exhibits two vulnerabilities of exposing 4G-3G network switch to adversaries. This can be further exploited to launch ping-pong attacks where mobile users may suffer from up to 91.5% performance downgrade, or 4G denial-of-service (DoS) attacks where mobile users are deprived of 4G LTE connectivity without their consent.
Threats from VoLTE
VoLTE can be exploited by the adversary to easily gain free data access, shut down continuing data access, or subdue an ongoing call, etc.. It can be also used to manipulate the radio resource states of the victim?s device in a silent call attack and thus consume unnecessary resource.
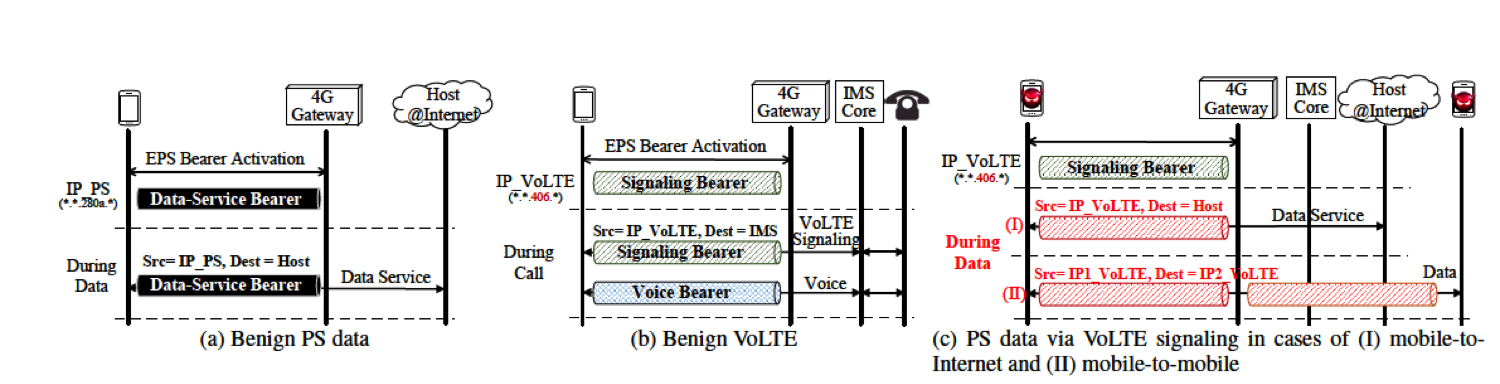
VoLTE makes it possible to carry data packets over VoLTE signaling channel. While VoLTE intends to use PS packets to carry signaling messages, it is never forbidden from turning PS data into VoLTE (signaling). Similar to the data service that retains a bearer (i.e., IP connectivity), VoLTE also has a signaling bearer for its control-plane operation. As shown in Figures 2a and 2b, both need to first activate a bearer and obtain an IP connectivity within the LTE network. Afterwards, data packets can be delivered through this bearer once any service starts. The device sets the source address as that allocated by the 4G Gateway and the destination as the target host?s. For VoLTE, upon any call request, SIP messages are exchanged between the device and the IMS core through the signaling bearer. It then on-demand invokes a voice bearer to carry conversation traffic if the call is accepted. When the call ends, the voice bearer is released. With the packet-carrying capability, it is feasible to carry any data through the VoLTE signaling bearer under two vulnerabilities. First, on the device side, there is no access control to prevent non- VoLTE packets from being injected into the signaling bearer. Second, on the network side, these injected packets are allowed to pass by (e.g., routed to the destination by the 4G gateway). This has been validated in two tier-1 US carriers. Moreover, with a distinct charging model, voice signaling messages are free and thus PS data over VoLTE signaling is free of charge! Unsurprisingly, the VoLTE-exploited data access can obtain higher, yet underserved priority. This is because the high priority is assigned to provide QoS for VoLTE. This hurts normal PS data services, particularly during network congestion. Similarly, on VoLTE voice bearer, junk packets can be injected to overwhelm the bearer and thus mute the ongoing calls.
We devise proof-of-concept attacks as showcases, and demonstrate their viability over operational LTE networks of Tier-1 US mobile carriers.
Threats from SMS over LTE
We identify one vulnerability in SMS over LTE. We uncover SMS sender spoofing in certain 4G LTE networks. Similar to VoLTE, SMS migrates from the circuit-switching technology to the full packet-switched design. SMS are carried through Session Initiation Protocol (SIP) over IP and implemented by IP Multimedia Subsystem (IMS). However, we uncover that some 4G LTE operators do not implement sufficient security mechanism so that SMS senderID can be spoofed. In particular, the operator does not implement network-layer or transport-layer security mechanisms to protect communication between mobile users and the IMS servers (e.g, IPSEC or TLS); instead, it uses the DIGEST for authentication (RFC3261). As a consequence, it becomes possible for an adversary to spoof SMS messages. On the other hand, most mobile service providers take one-way communication model to use SMS to authenticate the operations. For example, Facebook allows the user to send "like" to FBOOK(32665). Upon receiving it, Facebook will directly execute the operation of liking the page on "his/her" behalf. It will not check whether the SMS comes from the authentic users, but simply depending on the phone number. As a result, this vulnerability can be exploited to launch an individual attack (one certain user spoofing) or a large-scale of attack (many-user spoofing).
Demo
Free Data Service via VoLTE
This demo used Skype video conferencing as an example and demonstrated that mobile users could get free Internet data access in 4G LTE networks, if the phone supports the latest VoLTE feature. This attack exploits the vulnerabilities in current VoLTE deployment in mobile carrier networks and mobile phones. In this demo, Skype used 12.5MB in 1 minute but no data usage was charged (1MB gap caused by background traffic). It remained uncharged for 30 minutes.
Note: we have reported it to the carrier and now this attack has been fixed.
Voice DoS attack (muted voice) via VoLTE
This demo shows that VoLTE users will suffer voice-muted DoS attack during voice calls. Initially, caller and callee can make a voice call through; Afterwards (likely after 2-10 seconds), no one can hear each other. This attacks exploits the vulnerabilities in current VoLTE deployment in mobile carrier networks and mobile phones. The malware app (in the user space, without extra permission) can inject spam packets into VoLTE voice bearer so that authentic voice traffic is discarded.
Hack Facebook Via SMS over LTE
This demo discloses three proof-of-concepts attacks on Facebook. An attacker can "post" status, "like" a page, "add" a friend on Facebook on other's behalf without his/her consent. Namely, our FB account might be easily hijacked when an attacker sends SMS messages to FBOOK using spoofed sender ID in a contactless manner.
All-In-One Demo: HackCellular
We have developed an all-in-one-demo, called HackCellular, to replay identified threats in our recent work on your own phones. Source codes can be found in the link. The below is its video demo which records three attacks. The second and the third are Ping-pong attack and stuck-in-3G attack.
Due to security concerns, we do not release all the attacks to the public. Other attacks are available upon requests.
Publication
| How Voice Calls Affect Data in Operational LTE Networks MobiCom'13 Guan-Hua Tu, Chunyi Peng, Hongyi Wang, Chi-Yu Li, Songwu Lu |
| How Voice Call Technology Poses Security Threats in 4G LTE Networks CNS'15 Guanhua Tu, Chiyu Li, Chunyi Peng, Songwu Lu |
| Insecurity of Voice Solution VoLTE in LTE Mobile Networks CCS '15 Chi-Yu Li, Guan-Hua Tu, Chunyi Peng, Zengwen Yuan, Yuanjie Li, Songwu Lu, Xinbing Wang |
| New Threats to SMS-Assisted Mobile Internet Services from 4G LTE Networks arxiv Guan-Hua Tu, Yuanjie Li, Chunyi Peng, Chi-Yu Li, Muhammad Taqi Raza, Hsiao-Yun Tseng, Songwu Lu PDF |
| VoLTE*: A Lightweight Voice Solution to 4G LTE Networks HotMobile '16 Guan-Hua Tu, Chi-Yu Li, Chunyi Peng, Zengwen Yuan, Yuanjie Li, Songwu Lu |
| New Security Threats Caused by IMS-based SMS Service in 4G LTE Networks CCS '16 Guan-Hua Tu, Chi-Yu Li, Chunyi Peng, Yuanjie Li, Songwu Lu, |
Team Member
- Chunyi Peng (Purdue University)
- Songwu Lu (University of California, Los Angeles)
- Guan-Hua Tu (University of California, Los Angeles)
- Taqi Raza (University of California, Los Angeles)
- Xiaohu Zhao (Ohio State University)
- Yuanjie Li (University of California, Los Angeles)
- Zengwen Yuan (University of California, Los Angeles)
- Chi-Yu Li (University of California, Los Angeles)
Research Support
We gratefully acknowledge research support from NSF (CNS-1527613 and CNS-1528122) and the departmental support from OSU.


Any opinions, findings, and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of the National Science Foundation.